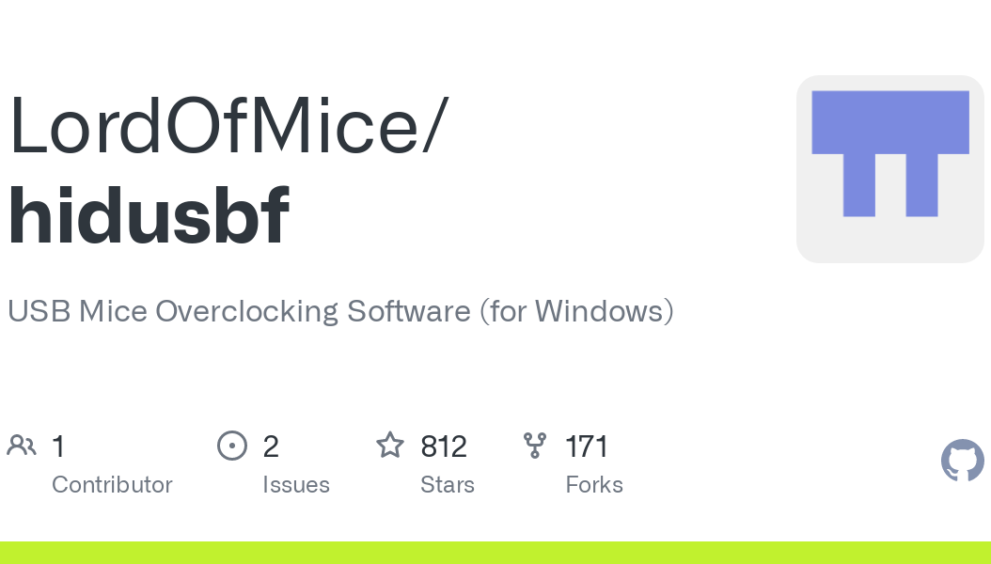
Exploring HIDUSBF: A Comprehensive Guide to USB Firmware Hacking
In the realm of technology and cybersecurity, understanding the intricacies of USB devices and their firmware is paramount. HIDUSBF, short for Human Interface Device USB Firmware, is a powerful tool that allows users to modify and customize the firmware of USB devices. In this article, we delve into the world of HIDUSBF, exploring its functionalities, applications, and the implications for security and customization.
Unveiling HIDUSBF: What is it?
HIDUSBF is a specialized tool designed to interact with the firmware of USB devices, particularly those classified as Human Interface Devices (HID). These devices include keyboards, mice, game controllers, and other peripherals that communicate with computers via the USB protocol. HIDUSBF enables users to access and modify the firmware code of these devices, offering unprecedented control and customization options.
Applications and Use Cases
The versatility of HIDUSBF opens up a myriad of applications and use cases across various domains:
- Customization: HIDUSBF allows users to customize the behavior and functionality of their USB devices. This can range from remapping keyboard keys to creating custom macros for gaming peripherals, enhancing user experience and productivity.
- Security Research: Security researchers and professionals utilize HIDUSBF to analyze the firmware of USB devices for potential vulnerabilities and security flaws. By reverse-engineering the firmware code, researchers can identify weaknesses and develop countermeasures to mitigate risks.
- Penetration Testing: Ethical hackers and penetration testers leverage HIDUSBF to assess the security posture of systems and networks. By manipulating the firmware of USB devices, testers can simulate attacks and evaluate the effectiveness of defense mechanisms against USB-based threats such as BadUSB attacks.
- Hardware Modification: Enthusiasts and hobbyists use HIDUSBF to explore hardware modification projects, such as creating custom USB peripherals or integrating additional functionality into existing devices. The tool provides a platform for experimentation and innovation in the realm of hardware hacking.
Risks and Considerations
While HIDUSBF offers significant potential for customization and security research, it also poses certain risks and considerations:
- Bricking Devices: Incorrectly modifying firmware can lead to device malfunction or “bricking,” rendering the device unusable. Users should exercise caution and thoroughly understand the implications of their modifications before proceeding.
- Security Implications: Modifying USB firmware, especially for malicious purposes, can have serious security implications. Users should adhere to ethical guidelines and legal regulations when utilizing HIDUSBF for security research or penetration testing.
- Manufacturer Support: Firmware modifications may void warranty agreements and negate manufacturer support for USB devices. Users should be aware of the potential consequences of firmware alterations on device warranties and support services.
Best Practices and Recommendations
To maximize the benefits of HIDUSBF while minimizing risks, users should adhere to the following best practices:
- Backup Firmware: Always create backups of original firmware before making modifications. This ensures the ability to revert to the original state if necessary.
- Verify Authenticity: Exercise caution when downloading firmware files and ensure their authenticity to mitigate the risk of malware or tampering.
- Community Engagement: Engage with online communities and forums dedicated to USB firmware hacking to share knowledge, seek advice, and collaborate on projects.








































































































































































































































































































































































































































































































































































































































![Fixing [pii_email_aa0fea1a78a192ae7d0f] Microsoft Outlook Error](https://www.huffenpost.com/wp-content/uploads/2023/03/What-Causes-the.jpg)
![Fixing [pii_email_aa0fea1a78a192ae7d0f] Microsoft Outlook Error](https://www.huffenpost.com/wp-content/uploads/2023/03/How-to-fix-the-1-1024x1024.webp)
![Quick fixes for the [pii_email_dbd9dd084703ead3b9cf] Mail Error](https://www.huffenpost.com/wp-content/uploads/2023/03/How-to-Avoid-pii_email_b6b14f95f44a83737071-Outlook-Error-1024x576.jpg)
![How to fix the [pii_email_bbf95bff57a974a71da8] in Microsoft Outlook?](https://www.huffenpost.com/wp-content/uploads/2023/03/How-To-Solve-The-pii_email_9e750e335dfd9d75badb-Outlook-Error.webp)
![How to solve the [pii_email_b6b14f95f44a83737071] Outlook Error](https://www.huffenpost.com/wp-content/uploads/2023/03/How-to-Avoid-pii_email_b6b14f95f44a83737071-Outlook-Error.png)
![Ways to fix the "[pii_email_1fb861393abed78ab415] Error](https://www.huffenpost.com/wp-content/uploads/2023/03/pii_pn_56e685559f213991c933-Error-Causes-and-Solutions2.jpg)
![How to Fix the [pii_email_e2f55b4aa7bb667da6d9] Error](https://www.huffenpost.com/wp-content/uploads/2023/03/How-to-fix-the.webp)
![What Everyone Should Know About [pii_email_59ea919492dfc2762030]](https://www.huffenpost.com/wp-content/uploads/2023/03/pii_email_aa0fea1a78a192ae7d0f-Email-Error-and-Its-Solutions-1024x683.jpg)
![How to Fix the [pii_pn_5359771d15a46e7b88bf] Outlook Email Error](https://www.huffenpost.com/wp-content/uploads/2023/03/pii_email_57a4a2f20ec6813a8481-SMTP-Error-Solution-2.jpg)